Discover Innovative Safety And Security with BQT Solutions for All Your Requirements
Discover Innovative Safety And Security with BQT Solutions for All Your Requirements
Blog Article
The Future of Security: Exploring the most recent Patterns in Electronic Safety Technologies
Digital safety modern technologies have become significantly sophisticated, providing ingenious remedies to address the ever-growing obstacles encountered by people and companies alike. From biometric authentication to the combination of artificial intelligence and device discovering, these fads hold the pledge of enhancing security steps in extraordinary methods.
Surge of Biometric Authentication
With the increasing need for secure and hassle-free authentication methods, the increase of biometric authentication has reinvented the means individuals gain access to and safeguard their delicate details. Biometric verification makes use of distinct biological features such as fingerprints, facial features, iris patterns, voice recognition, and also behavior characteristics for identity verification. This innovation provides a more dependable and safe and secure approach contrasted to typical passwords or PINs, as biometric information is unbelievably difficult to duplicate or take.
One of the vital benefits of biometric verification is its convenience. Customers no more need to bear in mind intricate passwords or stress over shedding accessibility due to failed to remember credentials. By simply using a component of their body for confirmation, people can promptly and firmly gain access to their tools, accounts, or physical areas.
Furthermore, biometric authentication improves safety and security by providing a much more robust protection versus unauthorized access. With biometric markers being special to every person, the danger of identification theft or unauthorized entrance is considerably lowered. This increased level of safety is especially crucial in sectors such as finance, medical care, and government where protecting sensitive info is vital.
Combination of AI and Machine Learning
The advancement of electronic safety technologies, exemplified by the increase of biometric authentication, has actually paved the way for improvements in the integration of AI and Artificial intelligence for boosted identification and defense devices. By leveraging AI algorithms and Device Discovering designs, digital protection systems can now assess vast amounts of data to detect patterns, anomalies, and potential hazards in real-time. These technologies can adjust to evolving safety hazards and provide positive reactions to mitigate threats properly.
One substantial application of AI and Device Knowing in electronic safety and security is in anticipating analytics, where historic data is used to forecast possible security violations or cyber-attacks. This proactive approach allows protection systems to anticipate and avoid dangers before they happen, improving total security procedures. Furthermore, AI-powered security systems can smartly monitor and assess video clip feeds helpful hints to recognize suspicious activities or people, improving action times and lowering duds.
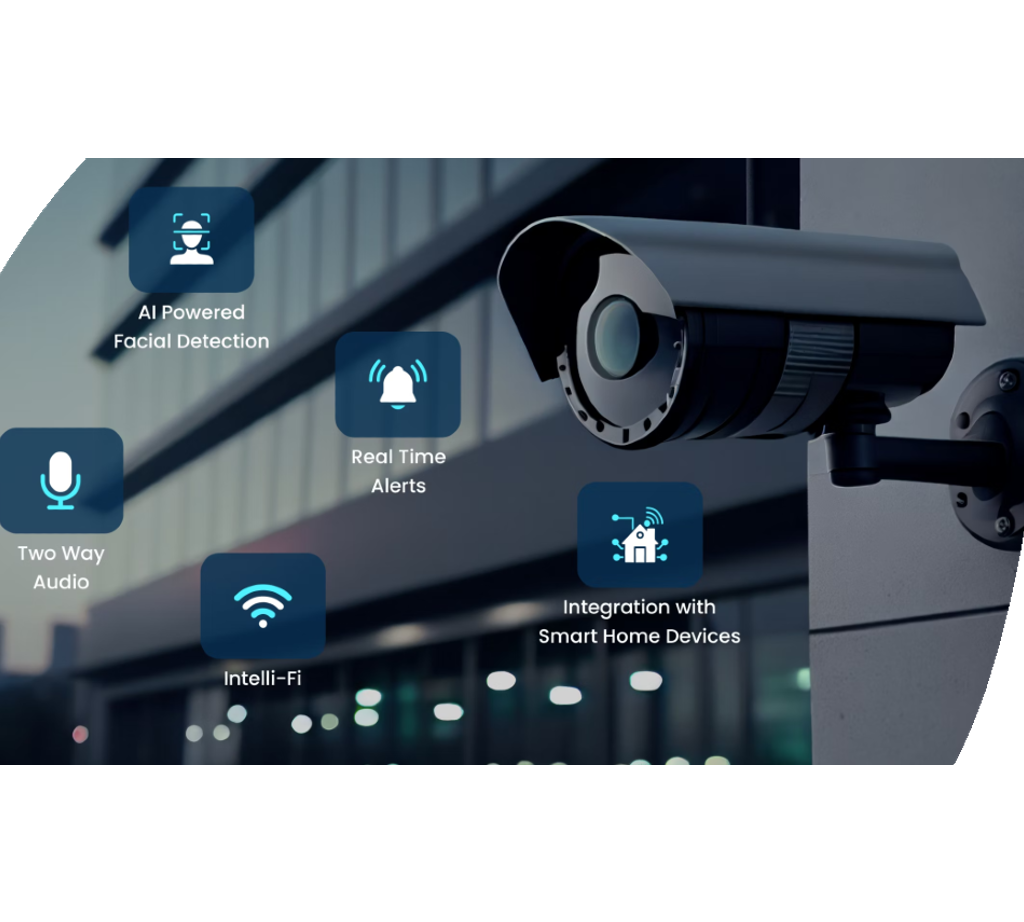
IoT and Smart Protection Instruments
Developments in electronic protection modern technologies have brought about the development of IoT and Smart Safety Instruments, changing the means protection systems operate. The Internet of Things (IoT) has enabled protection gadgets to be adjoined and remotely available, providing enhanced surveillance and control capacities. Smart Safety And Security Devices, such as clever electronic cameras, door locks, and activity sensors, are outfitted with performances like real-time informs, two-way communication, and integration with various other clever home systems.
Among the significant advantages of IoT and Smart Protection Instruments is the ability to give customers with smooth accessibility to their security systems through smart devices or various other internet-connected devices. This ease enables remote surveillance, arming, and disarming of safety and security systems from anywhere, supplying home owners with assurance and flexibility. Moreover, these gadgets commonly incorporate sophisticated attributes like facial acknowledgment, geofencing, and activity pattern recognition to enhance general safety and security degrees.
As IoT continues to progress, the integration of man-made knowledge and machine discovering algorithms into Smart Safety Instruments is expected to additional improve discovery precision and customization choices, page making electronic safety systems a lot more reliable and trusted.
Cloud-Based Protection Solutions
Emerging as a crucial element of contemporary electronic safety and security facilities, Cloud-Based Security Solutions provide unequaled flexibility and scalability in securing electronic possessions. Cloud-based safety and security options allow remote monitoring, real-time alerts, and streamlined administration of security systems from any type of place with an internet connection.
Moreover, cloud-based security services use automated software updates and upkeep, making sure that safety systems are constantly current with the most recent securities against emerging hazards. Generally, cloud-based safety and security options represent a cost-efficient and effective means for companies to improve their safety and security position and safeguard their digital possessions.
Emphasis on Cybersecurity Measures
With the increasing sophistication of cyber hazards, organizations are positioning a paramount concentrate on boosting their cybersecurity steps. BQT Biometrics Australia. As innovation breakthroughs, so do the techniques used by cybercriminals to breach systems and steal sensitive information. This has actually triggered companies to invest heavily in cybersecurity measures to protect their data, networks, and systems from malicious assaults
Among the crucial trends in cybersecurity is the fostering of sophisticated encryption methods to secure data both at rest and en route. Security aids to ensure that even if data is obstructed, it remains unreadable and safe and secure. Furthermore, the execution of multi-factor verification has come to be progressively usual to include an added layer of security and verify the identities of view it customers accessing sensitive details.
Verdict

Report this page